Cryptography Explained
Contents
Cryptography Explained Practical Everyday Applications Algorithms - Transforming Data Authentication with Public Keys Practical Uses of Asymmetric Crypto Integrity Protection Practical Uses of Hash Algorithms Data Privacy Protection Practical Uses of Symmetric Ciphers Cryptographic Keys and Key ManagementCryptography Explained
Cryptography is the art and science of secret writing. It is the foundation of online identity, privacy, and security. Only careful and well-executed application of cryptography will allow keeping private information hidden from prying eyes and ears. The origins of the term 'cryptography' itself stem from two words of the Greek language - κρυπτός (kryptós) meaning secret or hidden, and γράφειν (graphein) meaning writing.
Our modern world relies on electronic means for creating, storing, and transferring information. The security of this digital life owes much to cryptography. Cryptography intersects our daily lives in more ways people commonly realize.
Practical Everyday Applications
Our mobile phones, computers, online services, and nearly all personal online communications rely on different cryptographic algorithms and methods for the protection of the privacy and integrity of the identities and data involved.
Over the course of an ordinary day, we use many, sometimes rather advanced, cryptographic devices - there are smartcards in our wallets, laptops on our desks, mobile phones in our pockets, vehicle information systems in our cars, electronic locks on our doors, and so on.
Algorithms - Transforming Data
Cryptographic algorithms are the basic tools of this trade. An algorithm is a method or a technique that is applied to data. When an algorithm is used to encrypt (hide) the data, the readable information (often referred to as "plaintext") is transformed to an unreadable (encrypted) form. When an encrypted data (or "ciphertext") is returned to its readable form the process is called decryption.
Some algorithms are bi-directional (or symmetric) which means that the same algorithm (and key) are used for both encryption and decryption. In contrast, a one-directional algorithm works in only one way (ie. the operation cannot be reversed). An example of a one-directional cryptographic algorithm is a hash algorithm that produces a hash - a digital "fingerprint" of the processed data. The hash reliably identifies the origina data and no two data sets produce the same hash, yet this digital fingerprint cannot be turned back into the original data.
There are three main categories of these algorithms:
-
Public key cryptography algorithms
-
Data integrity protection algorithms
-
Symmetric cipher algorithms.
Roughly these three categories of algorithms cater for three different basic needs:
-
Reliable authentication (of users and other entities)
-
Data integrity protection
-
Protection of data privacy.
This division is somewhat of a simplification, but will serve for this article. For a more thorough analysis, see an authoritative source such as Applied Cryptography by Mr Bruce Schneier.
Authentication with Public Keys
While public key cryptography allows data encryption for privacy protection (and is used for that in some cases such as the PGP email protection scheme), it is cumbersome and computationally expensive to be used for bulk data protection. Instead, it is most commonly used to implement strong online authentication.
Strong authentication is the most prominent use case of public key cryptography, and in this role we (often unknowingly) use it daily.
Important concepts in public key cryptosystems are:
-
Key pairs that consist of a public key and a private key
-
Public key cryptography algorithms such as RSA, DSA, and ECDSA
-
Key lengths. For more information, see key size guidelines
Practical Uses of Asymmetric Crypto
Asymmetric cryptography and private/public key pairs are used extensively in smart card authentication, SSH public key authentication, and authenticating the servers of HTTPS-secured online services.
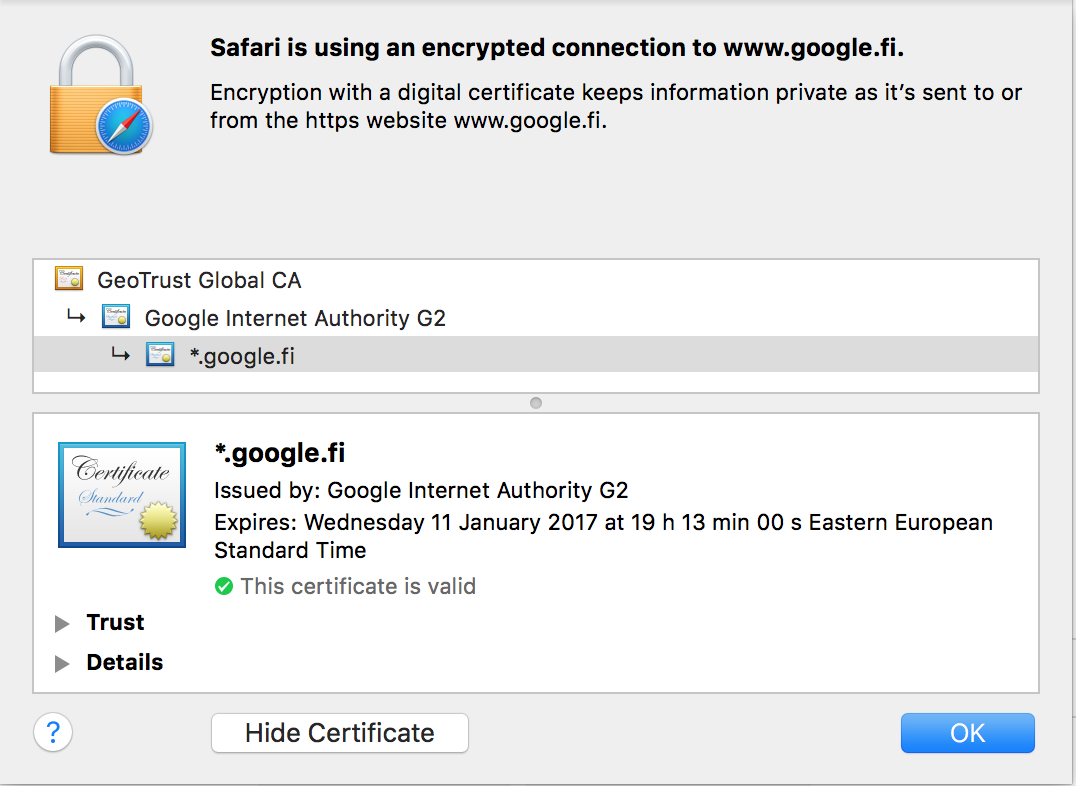
Asymmetric cryptography is the central technology behind Public Key Infrastructure (PKI) that allows scalable issuance, revocation, and management of digital certificates. Certificates are used for strong authentication, and digital signatures and they form the basis of trust for other security methods and protocols, such as SSL/TLS. PKI has sometimes been called the ID card office of the Internet, as PKI allows for reliable, 3rd party vouched for identity verification of peers that have not encountered each other before.
Integrity Protection
Our daily lives break down into amazing volumes of data every day - our health records, financial information, employment records, service subscriptions, and other parts of our everyday life, are recorded in and transmitted between various online systems. The fabric of our lives is dependent on the integrity of that staggering mass of data - every bit of this information must stay exactly as it is. The integrity of data keeps us alive - in some cases quite literally.
Cryptography offers methods for protecting and inspecting the integrity of digital data in the form of hashing and message digest algorithms. These one-way functions can take a given piece of data of arbitrary size and calculate a unique, small fingerprint of that data. This fingerprint, the hash, is unique to that particular piece of data, and even a tiny change in the data results in an entirely different hash. These hashes allow the detection of modifications in data and are an essential component of any cryptosystem that requires the protection of data integrity.
SHA-1 and SHA-2 are common hash algorithms.
Practical Uses of Hash Algorithms
Ensuring the integrity of data that has been received from online sources is one of the most common practical applications of hash algorithms. A rather simple and manual example of using hashes are various file download scenarios, where published hashes allow downloaders to verify the integrity of the file they receive.
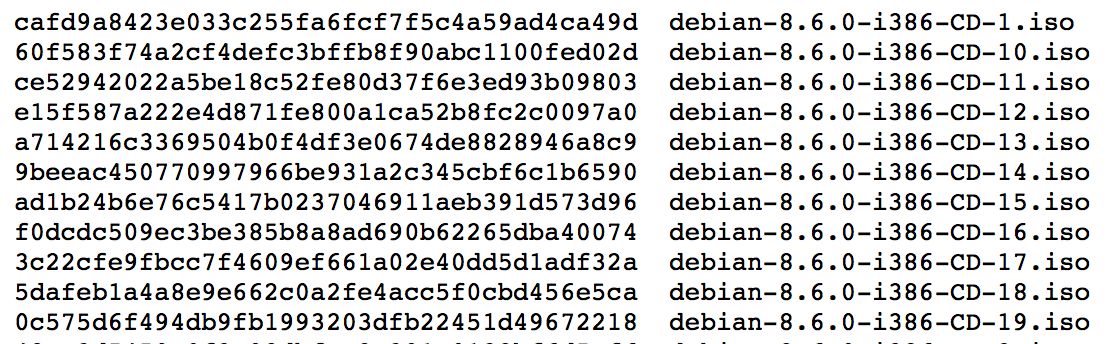
In a more advanced and automated way, the different hash algorithms have been integrated in secure communications protocols, virus scanners, content management systems, and e-commerce platforms. In these practical applications, cryptographic hashes and message digests are being used to ensure the integrity of data as it traverses between systems and networks.
Data Privacy Protection
The most common and probably easiest understood use of cryptography are the symmetric ciphers. A symmetric encryption algorithm is a method that renders data "hidden" when applied in one direction and returns the data readable when used in the other direction. The symmetric (secret) key functions like the password for the protected data. These algorithms are typically rather fast to execute, and they are used extensively to guarantee the privacy of data in network communications, databases/hard drives, and other applications where relatively large volumes of data need to be cryptographically processed in real time (or close to real time).
Since the key that is used for data encryption and decryption needs to be shared with each endpoint of the encrypted connection, or with every recipient of the encrypted data, the key generation and exchange are a critical feature of cryptosystems that use symmetric ciphers. A common key exchange mechanism in security protocols is the Diffie-Hellman key exchange.
Common symmetric ciphers are for example:
Practical Uses of Symmetric Ciphers
Symmetric ciphers are used in secure online communications in countless ways. The Virtual Private Networks (VPNs) that connect remote branches into a single corporate network protect data communications with protocols that use symmetric ciphers - encryption is the magic behind SSL, IPsec, SSH, and other network security protocols. Symmetric ciphers also protect data privacy in mobile telephony, most WiFi networks, and in practically every online banking and e-commerce service.
Data at rest solutions utilize fast symmetric encryption algorithms for encrypting disk contents against illegitimate use. A common encryption algorithm in this use case is the AES-XTS.
Cryptographic Keys and Key Management
A cryptosystem is a multiple of its parts - an essential security concern on any system is the way the encryption keys are managed. Even the strongest encryption algorithm offers no security if the attacker can get access to the encryption keys.
Enterprise networks in general have been designed with careful considerations for identity and access management. The guiding principles of providing access to resources based on the role of an individual (be it a user or a process) or of segregation of duties provide a starting point for a well-designed access control implementation. These principles need to be applied to practice in all aspects of enterprise access. So far the user-level access control has been in the spotlight of IAM, but in recent times the focus has been shifting towards the so far unaddressed issues of trusted access.

